Difference between revisions of "IT"
| Line 2: | Line 2: | ||
== Synergy Business Application == | == Synergy Business Application == | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
=== Web-Based Application === | === Web-Based Application === | ||
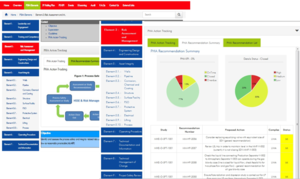
[[File:Technical Management of Changes (TMoC).jpg|thumb|none|'''Engeneering Change Management System (TMoC)''']] | [[File:Technical Management of Changes (TMoC).jpg|thumb|none|'''Engeneering Change Management System (TMoC)''']] | ||
| Line 70: | Line 51: | ||
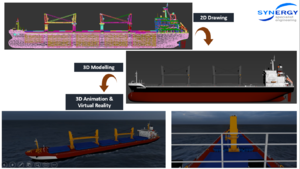
[[File:Ship.png||none|thumb|'''Ship 3D Animation & Virtual Reality''']] | [[File:Ship.png||none|thumb|'''Ship 3D Animation & Virtual Reality''']] | ||
Check the video through this link [https://synergylink-my.sharepoint.com/:v:/g/personal/itsupport_synergyengineering_com/EdsWWhVZQv1LrOceLSYd1TQBmvF5GF0noCZrGVD27Ibznw Ship] | Check the video through this link [https://synergylink-my.sharepoint.com/:v:/g/personal/itsupport_synergyengineering_com/EdsWWhVZQv1LrOceLSYd1TQBmvF5GF0noCZrGVD27Ibznw Ship] | ||
| + | |||
| + | == Synergy IT Services == | ||
| + | |||
| + | == Synergy Cyber Security == | ||
| + | |||
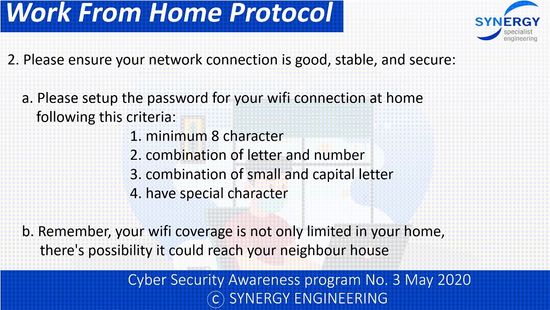
| + | Cyber Security Rules during Work from Home | ||
| + | [https://www.synergyengineering.com/ Synergy Engineering] work form home protocol: | ||
| + | [[File:Work Form Home Protocol.jpg|550px|none|none|Work Form Home Protocol-1]] <br> | ||
| + | [[File:Work Form Home Protocol2.jpg|550px|none|none|Work Form Home Protocol-2]] | ||
| + | |||
| + | == IT Management and Governance == | ||
| + | |||
| + | == IT Policy == | ||
| + | In doing a business activities, Synergy has regulations regarding information system security while using the company's hardware, software, and internet network. <br> | ||
| + | The regulation is made as a precaution against malicious attacks (viruses, malware, adware, spyware, etc), which can cause losses to the company like data corruption, data theft, data modification, and system failure. This regulation is also a guideline for access control, auditing, and monitoring that apply to our information, resources, and systems. | ||
| + | |||
| + | == Synergy Disruptive Technology == | ||
| + | |||
| + | == Our Solution for You == | ||
Revision as of 16:15, 24 June 2021
Synergy IT Infrastructure Capabilities
Synergy Business Application
Web-Based Application
Client :PT. Pertamina Hulu Energy Operation of South East Sumatera (PHE OSES)
Location : Indonesia
Project Type : Develop web-based application
Method : Agile
Scope of Work : Engeneering change management system
Year : 2020
Client : Pertamina Hulu Energi ONWJ
Location : Indonesia
Project Type : Develop web-based application
Method : Systems Development Life Cycle
Scope of Work : Process Safety Information Management
Year : 2016
Client : PT Santos Indonesia
Location : Indonesia
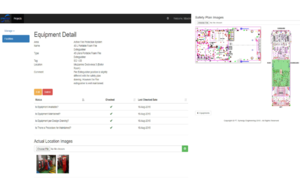
Project Type : FID Database
Method : Systems Development Life Cycle
Scope of Work : Seagood FPSO Facility Equipment Database
Year : 2015
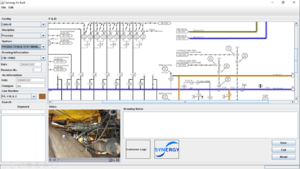
Desktop Application
Client : PT Santos Indonesiaa
Location : Indonesia
Project Type : Develop desktop application
Method : Systems Development Life Cycle
Scope of Work : As Built Drawing
Year : 2014
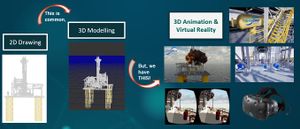
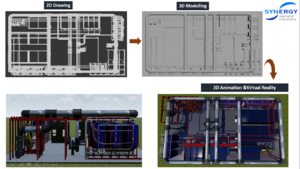
3D Animation & Virtual Reality
Here are some of our creation, we can convert 2D into 3D animation or virtual reality.
Check the video through this link Factory
Check the video through this link Ship
Synergy IT Services
Synergy Cyber Security
Cyber Security Rules during Work from Home Synergy Engineering work form home protocol:
IT Management and Governance
IT Policy
In doing a business activities, Synergy has regulations regarding information system security while using the company's hardware, software, and internet network.
The regulation is made as a precaution against malicious attacks (viruses, malware, adware, spyware, etc), which can cause losses to the company like data corruption, data theft, data modification, and system failure. This regulation is also a guideline for access control, auditing, and monitoring that apply to our information, resources, and systems.